Secure Access Service Edge (SASE, pronounced “sassy”) — defined by Gartner — is a security framework for enabling secure and fast cloud adoption, and helping ensure both users and devices have secure cloud access to applications, data and services anywhere, any time.
Digital business transformation flips network and security service design scheme, switching the focus point to identity of the user and/or device and not to Data Center, as it used to be.
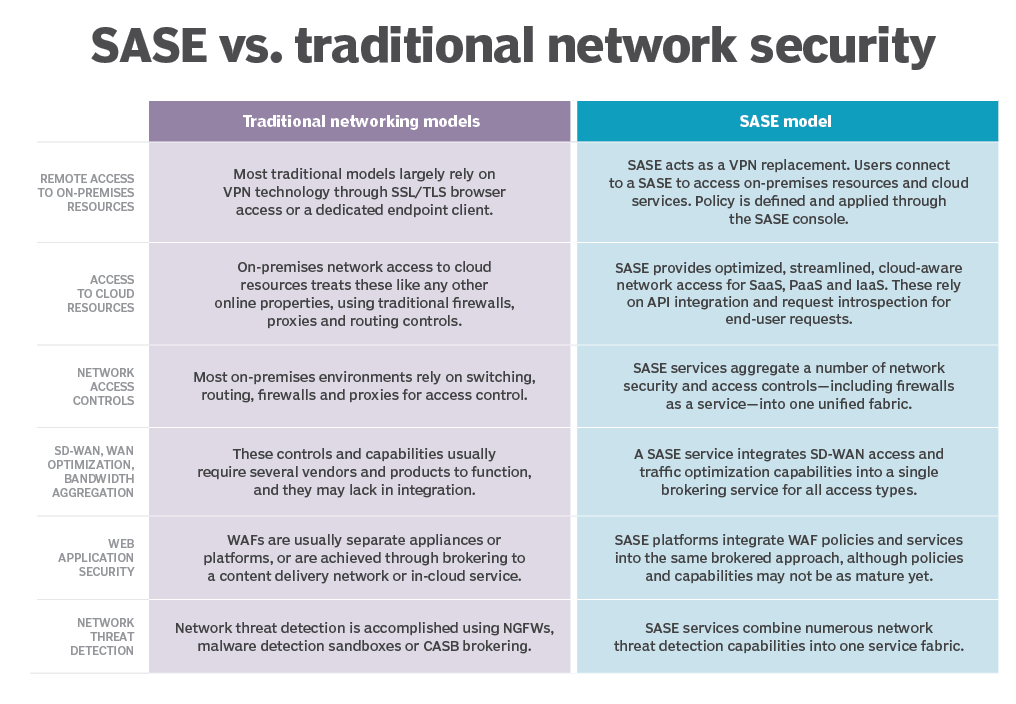
Today’s perimeter is no longer easily defined. The data center was once your network’s primary point of entry and exit, with more users, devices, applications, services and data located outside of an enterprise than inside.
Picture below shows how traditional perimeter and edge has moved and today it’s basically a “Dynamic Edge”.
84% of enterprises have a multi cloud strategy and 81% of them point to security as a major cloud challenge. Migration of applications and workloads to the cloud and profusion of endpoints across multiple environments led to expanding attack surface. From 2017 to 2019, there was a 73% increase in the number of organizations experiencing data breaches due to unsecured IoT devices or apps.

Network and network security architectures were designed for an era that is waning, and they are unable to effectively serve the dynamic secure access requirements of digital business. The enterprise data center is no longer the center of access requirements for users and devices. Digital Enterprises are characterized by:
- More user work performed off of the enterprise network than on the enterprise network
- More workloads running in IaaS than running in the enterprise data center
- More applications consumed via SaaS than consumed from enterprise infrastructure
- More sensitive data located outside of the enterprise data center in cloud services than inside
- More user traffic destined for public cloud services than to the enterprise data center
- More traffic from branch offices heading to public clouds than to the enterprise data center
Digital business transformation requires anywhere, anytime access to applications and services — many of which are now located in the cloud.
This brings CIO’s, CISO’s and risk managers into a need for converged cloud-native SASE (Secure Access Service Edge) solutions to address this shift.
A SASE solution provides mobile users, branch offices and retail locations with secure connectivity and consistent security wherever they are in the world. It does this by offering companies a single, centralized view of their entire network. This allows companies to quickly identify users, devices and endpoints, apply their networking access and security policies, and securely connect users to their applications and data in a cloud or mobile environment, all while ensuring multi-branch and multi-cloud network security.
It also enables companies to greatly reduce capital costs and cut the overhead typically associated with deploying security and networking at scale. More importantly, it speeds up deployment time and reduces the time to deliver protection by eliminating the need to set up traditional IT infrastructure.
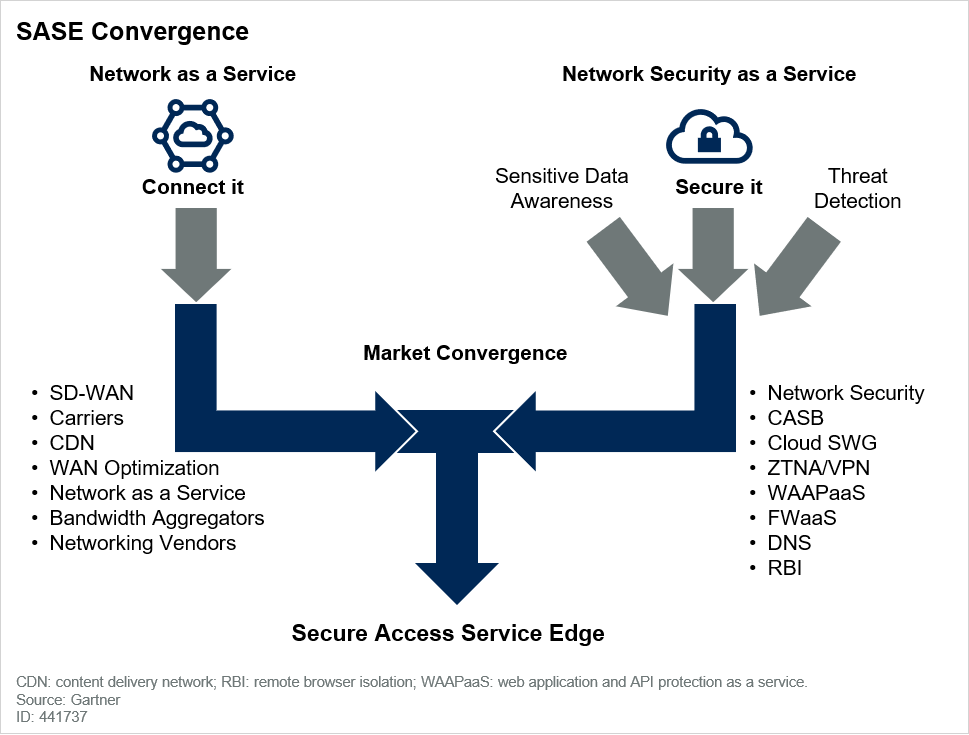
SASE converges the functions of network (SD-WAN, Carrier, CDN and more) and security services (such as SWG, CASB, FWaaS, and ZTNA) into a unified, global cloud-native service to support the dynamic secure access needs of digital enterprises. It is an architectural transformation of enterprise networking and security that enables IT to provide a holistic, agile and adaptable service to the digital business.
As a cloud platform, it connects and secures any type of edge device (such as a branch office, mobile device, IoT system, edge computing location) based on user identity and its real-time characteristics (device and location).
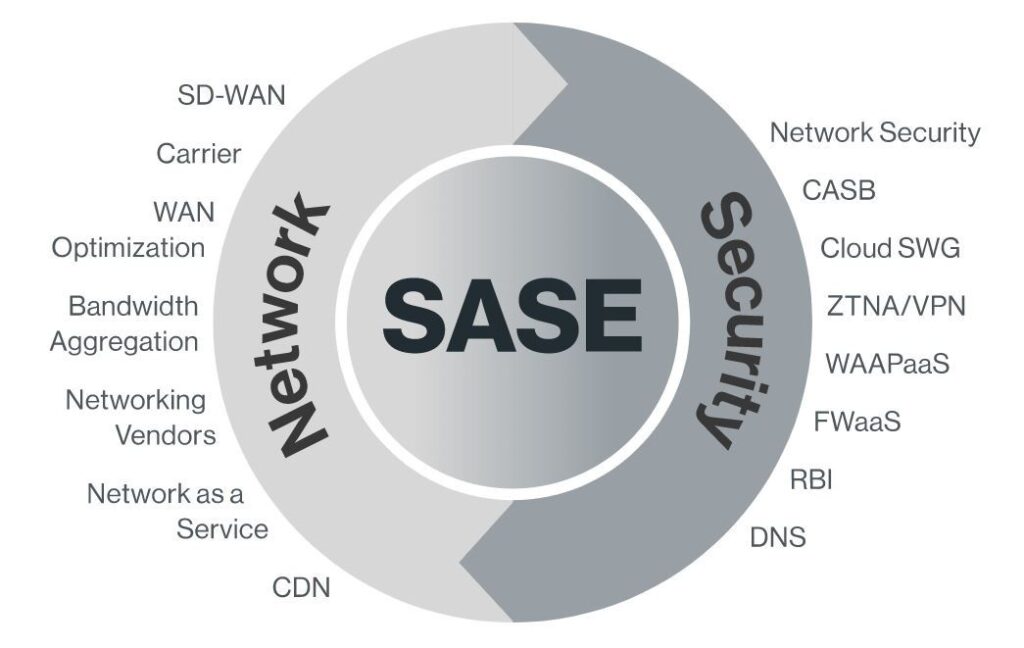
Solving emerging business challenges with point solutions leads to technical silos that are complex and costly to own and manage. Complexity slows down IT and its response to these business needs. SASE changes this paradigm through a new networking and security platform that is identity-driven, cloud-native, globally distributed, and securely connects all edges (WAN, cloud, mobile, and IoT).
With SASE, enterprises can reduce the time to develop new products, deliver them to the market, and respond to changes in business conditions or the competitive landscape.
A SASE architecture enables end-to-end security, whether the source is a remote worker, a branch location, or a headquarters. Threat prevention capabilities inherent to SASE include encryption of all communications, firewalls, URL filtering, anti-malware, and intrusion prevention systems (IPS). These capabilities are available to all connected network edges across the globe.
Gartner describes SASE as delivering services and enforcing policies as needed no matter where the entity requesting a service is located, nor what type of connection it has to the cloud.
According to the report, “The result is the dynamic creation of a policy-based, secure access service edge, regardless of the location of the entities requesting the capabilities and regardless of the location of the networked capabilities they are requesting access to.”
SD-WAN and SASE
A Software-defined Wide Area Network (SD-WAN) is a virtual WAN architecture that allows enterprises to leverage any combination of transport services – including MPLS, LTE and broadband internet services – to securely connect users to applications.
An SD-WAN uses a centralized control function to securely and intelligently direct traffic across the WAN. This increases application performance, resulting in enhanced user experience, increased business productivity and reduced costs for IT.
With traditional WAN solutions, organizations suffer a less than ideal quality of experience and have a hard time delivering high-performance bandwidth for critical applications. Since legacy WAN architectures rely on packet routing, they lack in-depth application visibility.
The SD-WAN solution can intelligently identify applications and determine the best path it should take to maximize functionality.
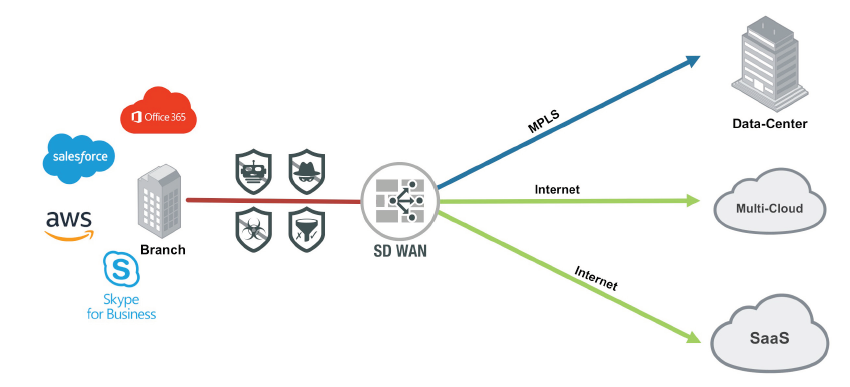
SASE combines an SD-WAN approach and security functionalities into one cloud-based service. SD-WAN features, like bandwidth optimization and traffic prioritization, are used by SASE. However, in an SD-WAN, virtualized devices spread throughout the WAN execute these features. In SASE, the cloud or a security agent on an end user’s computer makes networking decisions, such as where to send different applications’ traffic.
An element of SASE that sets it apart from SD-WAN is how it inspects traffic in an organization’s network. Instead of using service-chained point solutions, as SD-WAN does, SASE runs all security functions at once in multiple policy engines that make up a cloud-native software stack.
SASE architecture
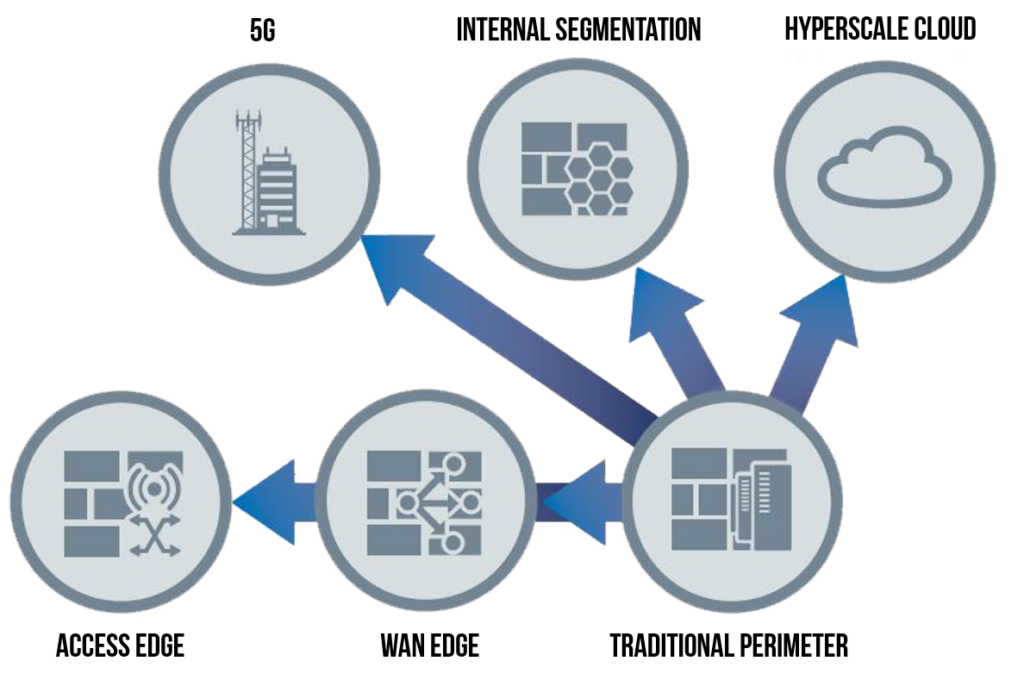
Instead of forcing various entities’ traffic to inspection engines entombed in boxes in the data center, we need to invert our thinking to bring the inspection engines and algorithms closest to where the entities are located. In a digital business, secure access decisions must be centered on the identity of the entity at the source of the connection (user, device, branch office, IoT device, edge computing location and so on).
As shown below, identities are the new center for access decisions, not the data center.
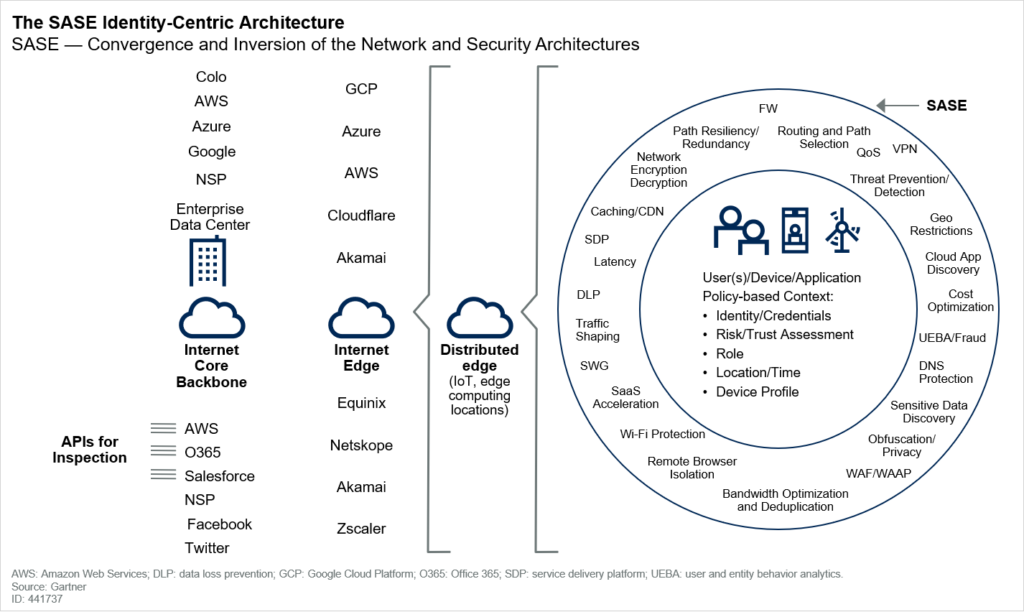
The identity of the user/device/service is one of the most significant pieces of context that can be factored into the policy that is applied. Other relevant sources include the location of the identity, time of day, risk/trust assessment of the device the user is accessing from, and the sensitivity of the application or data being accessed.
SASE delivers the required services and policy enforcement on demand, independent of location of the entity requesting the service and the access to the capability. The result is the dynamic creation of a policy-based, secure access service edge, regardless of the location of the entities requesting the capabilities and regardless of the location of the networked capabilities they are requesting access to.
Instead of the security perimeter being entombed in a box at the data center edge, the perimeter is now everywhere an enterprise needs it to be — a dynamically created, policy-based secure access service edge.
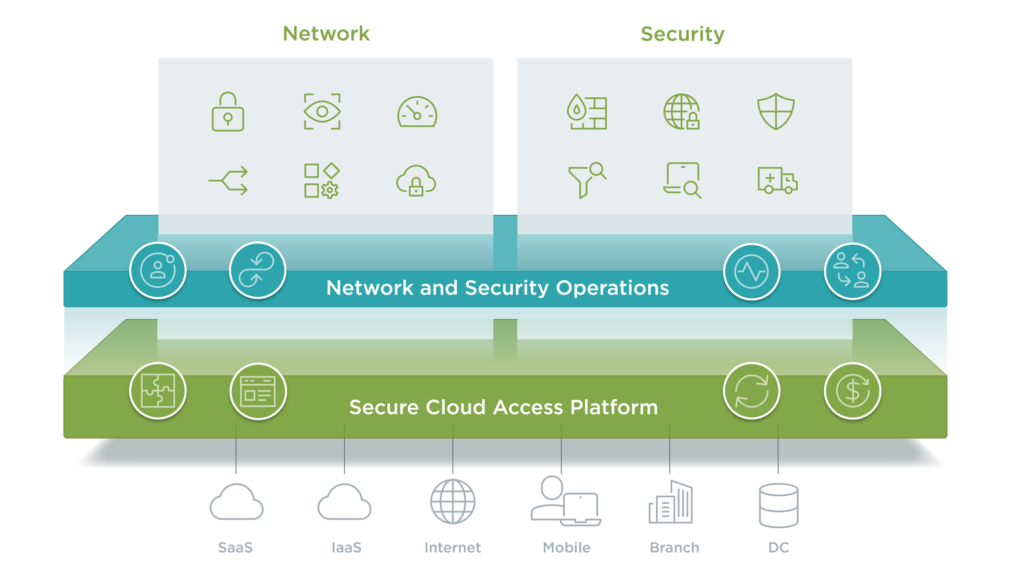
Benefits of SASE
There are numbers of benefits of SASE, but if I would have to chose, my favorite would be that it allows users to immediately gain secure access to a company’s network, wherever they are and whatever device they use.
Reduction in complexity and costs: SASE is consolidating network and security services which lowers the total number of vendors, physical or virtual appliances and agents, maintenance contracts, etc. By doing so, it dramatically reduces the cost, both capital and operational.
Enabling new digital services: SASE services will enable enterprises to make their applications, services, APIs and data securely and easily accessible to partners and contractors, without the risk exposure of legacy VPN and DMZ architectures. This will lead to increase of new business and opportunities for enterprises.
Increased Performance: Leading SASE vendors will provide latency-optimized routing across worldwide PoP’s. Based on policy, users can be routed through the provider’s high-bandwidth backbones.
Ease of use: SASE will reduce the number of agents required on a device to a single agent or device and automatically apply access policy without requiring user interaction. This provides a consistent access experience for users, regardless of where the user is, what they are accessing and where it is located.
Less overhead: due to the fact that SASE vendors run and maintaining the security engines. IT is freed from the updating, patching, and scaling appliances.
Centralized policy with local enforcement: Cloud-based centralized management with distributed enforcement and decision making.
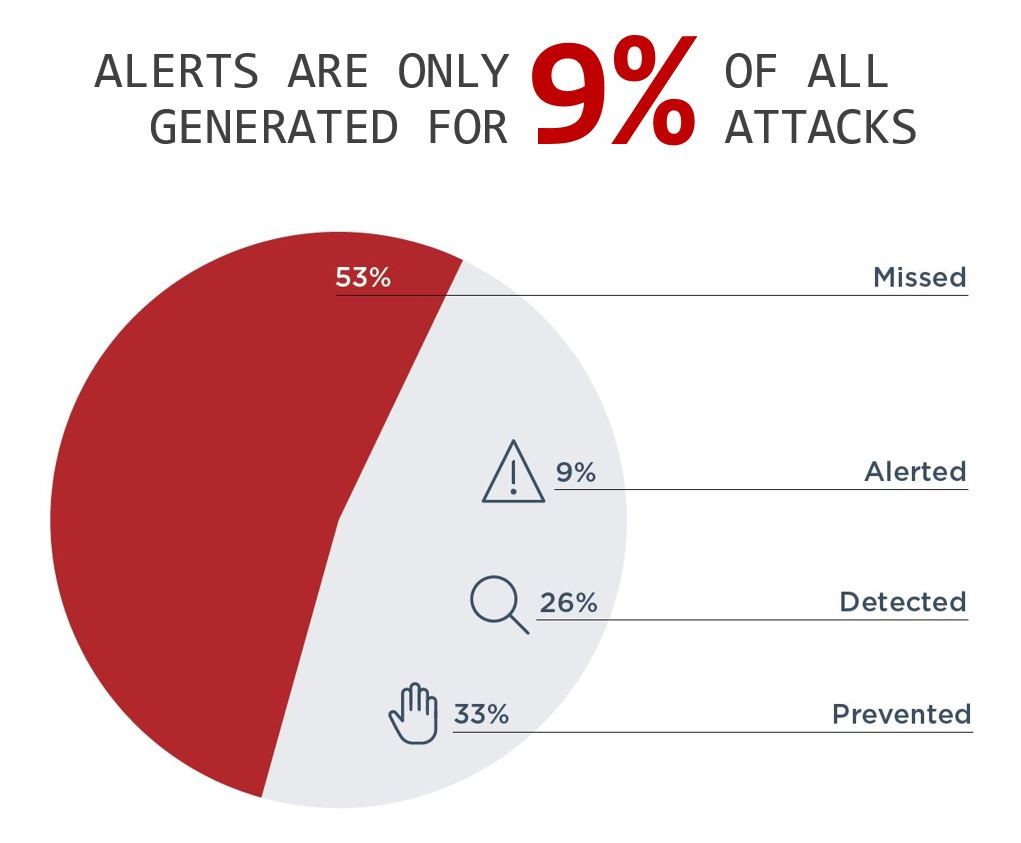
Last, but not the least and very much important is, Improved security, as shown below.