SSL encryption is an essential factor in keeping network communications secure. However, while SSL encryption has proven its value, the encrypted data also results in blind spots for security appliances. Organizations must decrypt and analyze SSL traffic to ensure that it is not used as a conduit for hackers to transport and distribute malware.
The SSL (Secure Sockets Layer) protocol and its modern, more secure replacement TLS (Transport Layer Security), are used to encrypt web traffic. Encrypting data in transit is standard practice, with approximately 90% of web pages now being encrypted. Although this helps prevent data breaches, cyber criminals use these encrypted channels to propagate malware and exfiltrate data, knowing they can bypass traditional security inspection solutions that don’t decrypt traffic.
Security inspection tools such as next-gen-firewalls (NGFW), data-loss protection (DLP) systems, intrusion detection/protection systems (IDS/IPS), web gateways, and others are great at finding threats within traffic. However they do not efficiently decrypt traffic before inspecting. This leaves security inspection tools blind to encrypted threats, and allows malware or intellectual property data to flow through without being inspected or stopped where appropriate. SSL Decryption, also referred to as SSL Visibility, is the process of decrypting traffic at scale and routing it to various inspection tools which identify threats inbound to applications, as well as outbound from users to the internet.
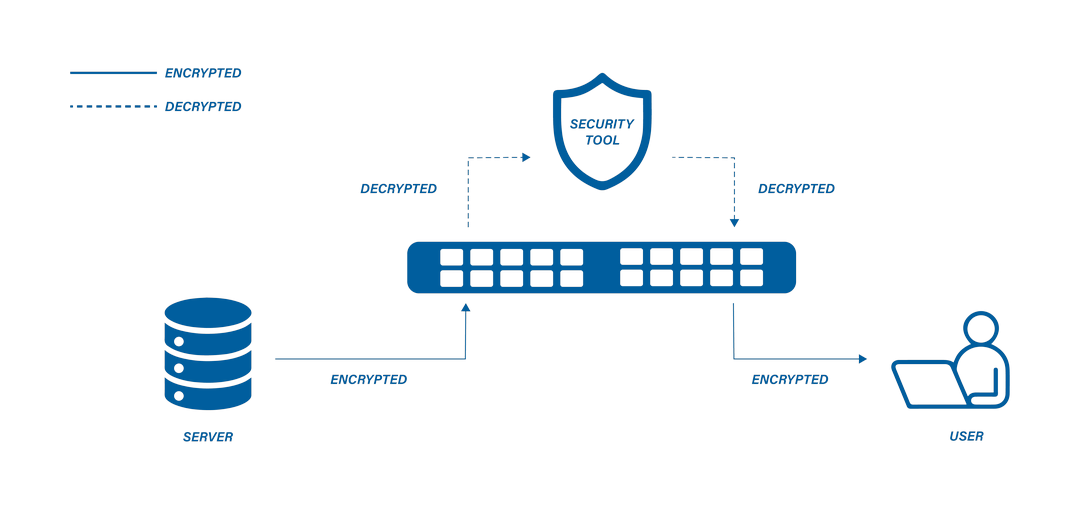
The X3-Series supports in-line and passive SSL/TLS traffic decryption. The TLS decryption feature reduces blindspots that exist with encrypted traffic. X3-Series network packet brokers support passive decryption of TLS 1.2 and below. TLS 1.3 in-line decryption is done via a proxy. Decrypted traffic can be sent to an out-of-band security or analysis appliance.
After the monitoring data has been decrypted, it can be forwarded to network monitoring tools like IPS, IDS, protocol analyzers, SIEMs tools, etc. This reduces the load on these tools, allowing them to maximize their speed and capacity and the applications they run, such as sandboxes and IPS.